What Are The Steps Of The Information Security Program Lifecycle Dod

The six steps of the pdlc are analyse the problem design the program code the program test and debug the program formalize the solution and maintain the program.
What are the steps of the information security program lifecycle dod. This course provides an introduction to the department of defense dod information security program. Rmf for is and pit systems. The department of defense dod acquisition process is one of three 3 processes acquisition requirements and funding that make up and support the defense acquisition system and is implemented by dod instruction 5000 02 operation of the adaptive acquisition framework. This course will provide a basic understanding of the program the legal and regulatory basis for the program and how the program is implemented throughout the dod.
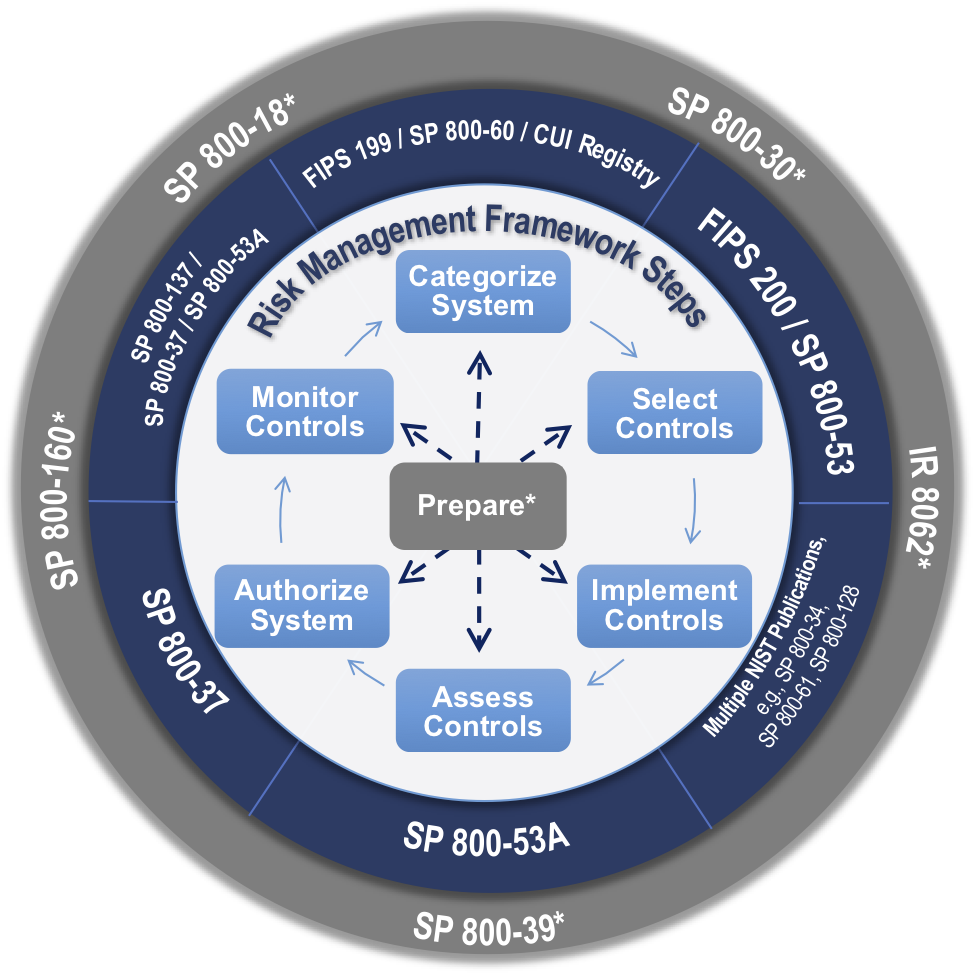
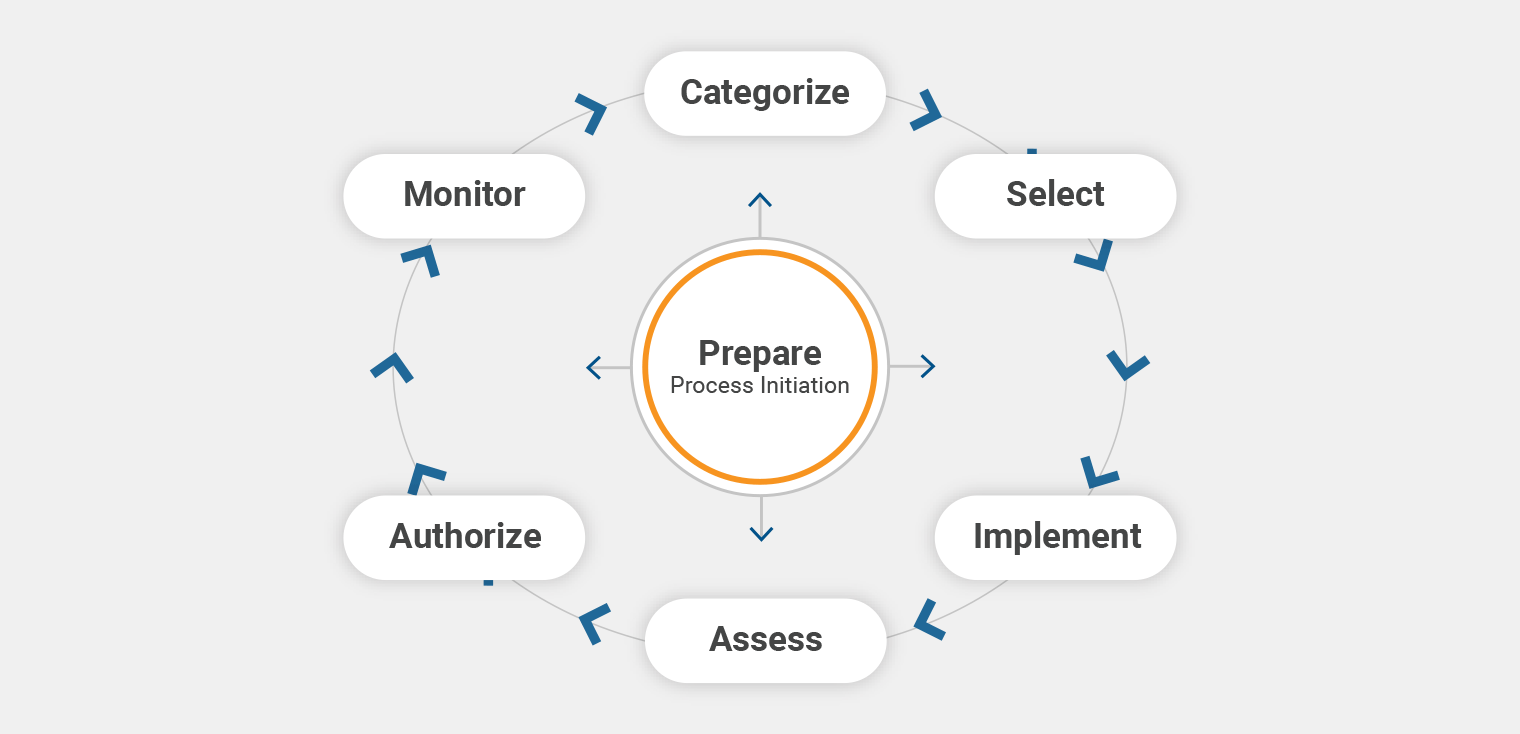
This instruction provides the policies and principles that govern the defense acquisition. Life cycle management lcm life cycle management is the implementation management and oversight by the designated program manager pm of all activities associated with the acquisition development production fielding sustainment and disposal of a dod system across its life cycle jcids operation manual. The most crucial steps for engineers are always the earliest ones. Categorization and selection of security controls steps 1 and 2 so those steps of the rmf will be discussed in more detail here.
What are the steps of the information security program life cycle. Assigning a lower classification level to classified information because the information requires less protection in the interest of national security. Students will be provided with a basic understanding of the legal and regulatory basis for the program how the program is implemented throughout the dod and an introduction to the information security program lifecycle. During this course you will learn about the dod information security program.
Students will be provided with a basic understanding of the legal and regulatory basis for the program how the program is implemented throughout the dod and an introduction to the information security program lifecycle. Dod information security program. Classification safeguarding dissemination declassification and destruction the unauthorized disclosure of confidential information could reasonably be expected to cause to our national security. The records disposition program provides life cycle management of all osd records regardless of form or content from creation to destruction for temporary materials or transfer to the custody of the national.
It covers the information security program lifecycle which includes who what how when and. The records management program mission is to oversee the operation of the records disposition for the office of the secretary of defense the osd components and field operating agencies.