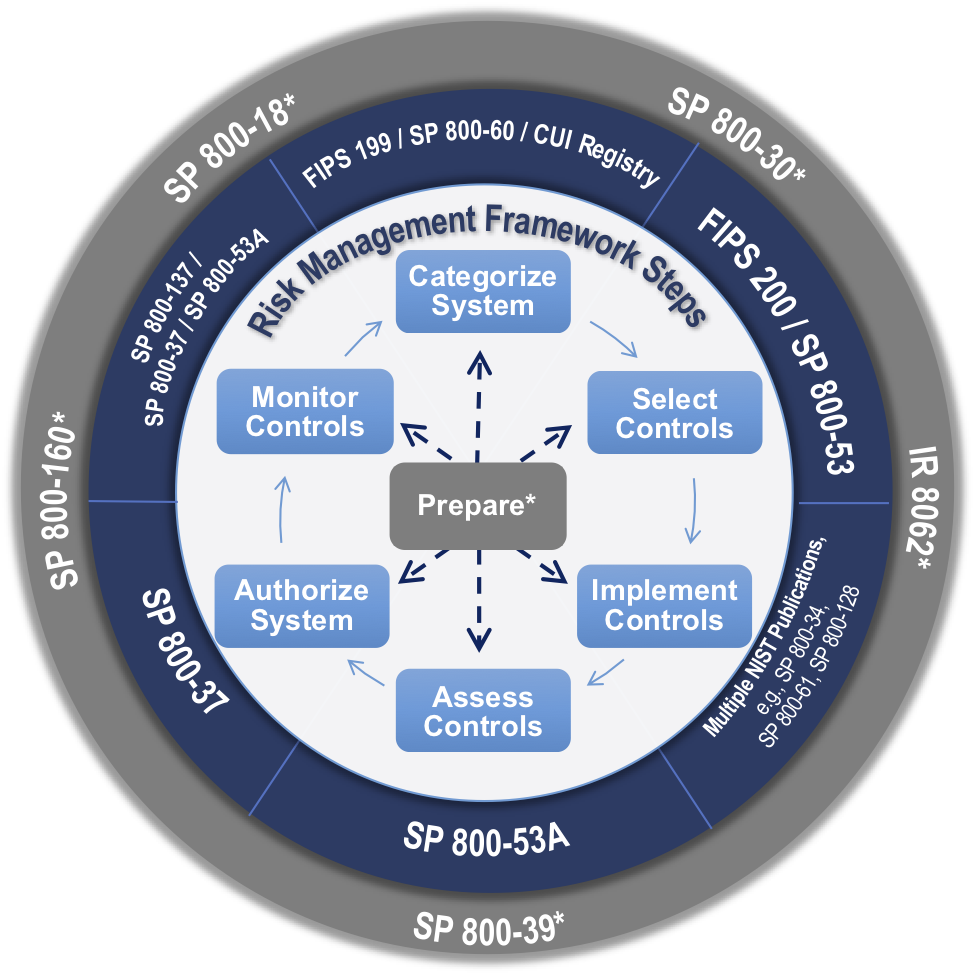
What Are The Steps Of The Information Security Program Lifecycle Stepp

The information security lifecycle identify assess protect and monitor linkedin twitter youtube facebook like most sectors of it security professionals can follow a lifecycle model throughout their daily work lives.
What are the steps of the information security program lifecycle stepp. During this course you will learn about the dod information security program. Introduction to information security. It covers the information security program lifecycle which includes who what how when and. It is important to understand that a security program has a continuous life cycle that should be constantly.
Step one plan step two do step three check step four act. However most security professionals will tell you that they do not work in a linear and static fashion. Classification safeguarding dissemination declassification and destruction. We agree with this statement but we also believe that these life.
The six steps of the pdlc are analyse the problem design the program code the program test and debug the program formalize the solution and maintain the program. Students will be provided with a basic understanding of the legal and regulatory basis for the program how the program is implemented throughout the dod and an introduction to the information security program lifecycle. The steps of the information security program lifecycle are. Are the steps of the information security program lifecycle.
This course will provide a basic understanding of the program the legal and regulatory basis for the program and how the program is implemented throughout the dod.